For Immediate Release:
Dateline: San Luis Obispo,
CA
Friday, July 5, 2019
Burgess Forensicshttps://burgessforensics.comComputer Forensics, Electronic Discovery & Expert WitnessFri, 14 Jun 2019 19:50:47 +0000en-UShourly1https://wordpress.org/?v=5.0.4- The Case of The Client Who Wanted … to be Wantedhttps://burgessforensics.com/the-case-of-the-client-who-wanted-to-be-wanted/https://burgessforensics.com/the-case-of-the-client-who-wanted-to-be-wanted/#respondSun, 19 Aug 2018 02:21:34 +0000https://burgessforensics.com/?p=11068The Case of The Client Who Wanted … to be Wanted copyright Steve Burgess, 2018 It was nearly Christmas, but the morning sun was pouring in […]
The post The Case of The Client Who Wanted … to be Wanted appeared first on Burgess Forensics. ]]>The Case of The Client Who Wanted … to be Wantedcopyright Steve Burgess, 2018 It was nearly Christmas, but the morning sun was pouring in through the windows of my Central Coast office, casting shoe-shaped shadows on the West side of my desk. Perhaps I should have instead been thinking of a Night before Business, while visions of fuller sums danced through my head. The concept of the bills stacking up in my desk drawer began to draw my attention. But in my reverie, my mind went back to the days of sandals and long, carefree afternoons at UCSB. Then another shadow fell across the desk, obscuring thoughts of debtors and echoes of Birkies. It was Alicia D’Languissant, an Earth Mother from another era, with a snaggletooth grin, Ben Franklin specs, long gray hair falling over the shoulders of her tie-dye, with much-loved Birkenstocks peeking out from worn, baggy, bell bottoms. I was tempted to talk of wasting away those carefree hippie days, but then I snapped back to reality. I’m a forensicist and we’re bred to be too tough to care. So I took Jimi asking if I was experienced off the iTunes and asked, “How may I help you, Ma’am?” “Someone’s been hacking my computer, and I know who it is.” Alicia, long without a main squeeze, had spent a night of revelry a couple hundred miles north at a hotel in Sebastopol. It seemed too good to be true and when the lights came up in the morning, our man was nowhere to be found. So she thought. Soon there was correspondence and the beginnings of what might have blossomed into something fresh, something new, something groovy. Alas, it was not to be. Correspondence got spotty, and then went away. But secret visits started to proliferate. There were hints of unauthorized access to her laptop, and Alicia reported possible break-ins with doors left ajar. We made the contract, and I tucked into her computers. The first thing to do was to make a forensic working copy of the laptop’s hard disks. I might have pulled the hard drive from the laptop, attached it to a Tableau TD2U Forensic Imager, but Alicia wanted the computer left unopened. So instead I booted the laptop with a Kali Linux build containing CyanLine’s MinDAS Disk Acquisition System. With a couple of forensic working copies in hand, the Ms. was free to take her devices back to her home office for work. Using Magnet Forensics’ IEF, we extracted data from the Windows Registry to see what other USB devices might have been attached to the computer, but all of the devices that turned up were known and owned by D’Languissant We searched every which way for keyloggers, rootkits, Trojans, VPNs or any other remote access malware and logs of logins. But with three antivirus programs installed and solid passwords, it was one of the cleaner systems we had worked on. All logins appeared to be by her User account. Guest access was disabled. There were no incorrect password attempts. It was as clean as the flute solo in California Dreamin’. Using various keyword searches in EnCase, I also searched for remnants of old malware scans in order to turn up any that might have been previously detected and removed, as well as any references to LogMeIn that might show IP addresses from remote access sessions. There was a small amount of adware… These are relatively harmless, although possibly unwanted. They are not a source of remote control or malicious spying. They tend to get installed by websites and software, designed to deliver advertisements to you when you are browsing the web. We checked the header from the one email she had from her potential paramour. But it was Gmail and IP addresses from those headers always resolve to Google HQ. We found the IP address for the hotel from that one hot evening, but with no way to tell what room it had come from. She had checked out, but in her mind’s eye she was unable to leave. To go into either Google or the hotel’s records would have required a subpoena, but it turns out that several lawyers had already turned our bespectacled goddess down, and the cops didn’t even want to hear it. Alicia said that there had to be a way. Already a couple grand into the process, she said she could draw on her recent inheritance. I suggested that maybe there wasn’t anything to be gained in spending the money to dig further into the computer. Sometimes there’s just nothing to be found (even if someone has gotten unauthorized access). She was sure someone was watching her, and again, she was sure she knew who. She was sure He was plotting with his friends on the DarkWeb. I found him on Twitter and found that he had mentioned her once or twice, but not by name. He was laughing about being stalked by just one person, clearly by her. They say that one is the loneliest number, and perhaps it was her loneliness creating a fictional suitor. Alicia had dug deeply into her computer’s logs and brought in several printouts she had made of suspicious-looking activities on the computer. Indeed, some of the names of the activities would appear to the layperson to be suspicious. Router Advertisements, Remote Volume Management, Secure Socket Tunneling Protocol (SSTP), and Remote Management Services were all set to optimal configurations to be protective of her system. The Windows Vault was normal. There were no large or unusual files that might indicate a stealth partition. I hated to burst her bubble, break her heart, and speak of what a fool believes. Using my diplomatic best I tries to persuade her that we ought to drop this line of inquiry. But she was not to be deterred. Another sunny afternoon, and Alicia’s SUV comes bombing into the parking lot. Leaving the car running, she jogs into my office and says I have to go out to her car, RIGHT NOW. “He’s hacked the entertainment center on my car and changed the lyrics to this David Bowie song!” Reserving judgement (or at least, trying to keep it from showing on my face), I head out to witness the offending music. “Alicia, I’m sorry, but that’s Lou Reed and Velvet Underground. Come in and listen while I ask iTunes to review it for us.’ No, the lyrics to Sweet Jane were just what they’d always been. As I told her in my report, “At least from the evidence I have reviewed, I think you have not been cyberattacked.” Some people can’t take “you’re safe” for an answer. She soon came back for another visit, because when she approached the TVs at the department store, the video displays changed channels to news stations that had hidden references to her and to the inamorato as she approached. Without even playing a record backwards. Perhaps chemicals from the past had caught up with her. I urged her to save her money and to let me speak with her sister, and she gave me permission. I shared the results of my work for Alicia with her sis. It turns out that this series of events wasn’t happening in a vacuum. Little sister had power of attorney due to past erratic behavior, and it was just another day in the life. The thing is, when a person thinks they’ve been hacked and talks about it, people tend to think they’re on the crazy train. But people do get hacked all the time. Still, most of the hacking isn’t targeting us specifically, but is usually either targeted at millions of people to populate botnets and the like, or to hack a database with lots of credit card numbers or identities for use in fraud. Very few of us are really important enough to be individually targeted (I know I’m not). Although we all might think that we’re king of the world, we’re mostly ordinary, average guys. If there are signs of hacking, looking into it is a good idea, but it needs to be with an open mind. It’s important when reporting it not to assume agency by a particular person. Rather than say, “He did this,” “She did that,” one will be taken much more seriously by talking about the symptoms and not asserting whodunit. Most (but not all) of what appears a hacked phone or computer is rather a compromise of their online account or social media. In this case though, it seemed our desperate heroine was projecting and wanting hear her man say he was the one who was “crazy on you.” Alicia’s rig was clean, sister got her some help. Much money was left unspent and so didn’t make its way to my pocket. But what do I care? I have sunshine and shadows. I’ve got 75 degrees. I’ve got some puzzles to solve. Now that this case is solved, I’ve got some peace and quiet, because I’ve also got a phone that needs to ring a little more. I’m ready to do the forensic magic man thing again and catch some nonfiction digital bad guys. Bring them on. This is just one of the many “CSI – Computer Forensics Files: Real Cases from Burgess Forensics.” Stay tuned for more deeds good & bad uncovered by science. The post The Case of The Client Who Wanted … to be Wanted appeared first on Burgess Forensics. ]]>https://burgessforensics.com/the-case-of-the-client-who-wanted-to-be-wanted/feed/0 - Burgess Forensics Newsletter Vol. 5 Issue 1: FitBit Fun Forensics & Foes 08.08.2018https://burgessforensics.com/burgess-forensics-newsletter-vol-5-issue-1-fitbit-fun-forensics-foes-08-08-2018/https://burgessforensics.com/burgess-forensics-newsletter-vol-5-issue-1-fitbit-fun-forensics-foes-08-08-2018/#respondWed, 08 Aug 2018 21:39:08 +0000https://burgessforensics.com/?p=11040 Fitbit, Fun, Forensics, and Foes Have you tracked your 10,000 steps today? Has anyone else tracked them? Fitness trackers are big business, helping people get and […]
The post Burgess Forensics Newsletter Vol. 5 Issue 1: FitBit Fun Forensics & Foes 08.08.2018 appeared first on Burgess Forensics. ]]> Fitbit, Fun, Forensics, and Foes Have you tracked your 10,000 steps today? Has anyone else tracked them? Fitness trackers are big business, helping people get and stay fit, and helping them share their progress with friends – and sometimes with strangers. 
As people are leaning more and more towards the digital world, cybercrime is becoming an issue that cannot be ignored … There are various types of attack that could occur and for many reasons, but one thing is for sure, you don’t want to be the victim of a cybercrime. I’ve Been Hacked: What Do I Do Now? We get this question several times a week, so it’s not just you. And no, it doesn’t mean you’re crazy – even if your friends think so, and even if law enforcement won’t take your case. People’s computers and phones get hacked, every day. Why won’t the police do anything about it – isn’t it a crime? Around the Realm Fun Facts The most common password is still “123456” !! Right now, one BitCoin is worth $6,319 (this will have changed by the time you read it).
Just over a year ago it was $2,874. Between now and then, it got to $13,860

More than $1 Billion in cryptocurrency has been stolen this year. 4 million BTC are lost, and 2 million BTC are stolen (out of 17.1 million in circulation) The post Burgess Forensics Newsletter Vol. 5 Issue 1: FitBit Fun Forensics & Foes 08.08.2018 appeared first on Burgess Forensics. ]]>https://burgessforensics.com/burgess-forensics-newsletter-vol-5-issue-1-fitbit-fun-forensics-foes-08-08-2018/feed/0 - The Rise of Cybercrime and How to Prevent Ithttps://burgessforensics.com/the-rise-of-cybercrime-and-how-to-prevent-it/https://burgessforensics.com/the-rise-of-cybercrime-and-how-to-prevent-it/#respondWed, 08 Aug 2018 20:51:36 +0000https://burgessforensics.com/?p=11036The Rise of Cybercrime and How to Prevent It (guest article contributed by Josh Wardini, of Webmastersjury.org) As people are leaning more and more towards the digital […]
The post The Rise of Cybercrime and How to Prevent It appeared first on Burgess Forensics. ]]>The Rise of Cybercrime and How to Prevent It(guest article contributed by Josh Wardini, of Webmastersjury.org) As people are leaning more and more towards the digital world, cybercrime is becoming an issue that cannot be ignored. Although many individuals and businesses are doing all they can to prevent such attacks, there is still a big risk that attackers may get in. There are various types of attack that could occur and for many reasons, but one thing is for sure, you don’t want to be the victim of a cybercrime. Cybercrime can be described as a type of criminal activity that involves a computer, networked device, and a network. The primary impact of this sort of crime is financial, and businesses have lost millions by attackers managing to breach their security. - Difficulty of getting caught – There are literally tens of thousands of internet criminals out there, the majority of which will never get caught. They don’t have to be internet geniuses, they quite simply have to lack morals and be willing to take a risk. Due to the vastness of the internet and the many ways fraud can be committed, it is very difficult for these criminals to get caught.
- Across Border Crimes – Unlike other crimes, most crimes on the internet will take place across international borders. Therefore, any law enforcement is always limited to jurisdictional boundaries. For example, if the FBI knew that a crime is being committed by someone in China, it can’t just travel to China to arrest the individual, it would have to go through a set of time consuming procedures first.
- Lack of Training – Many businesses fail to provide employees with security awareness and training regarding cybercrime. This means that the majority of people in a company will not know the best practises for preventing, spotting, and stopping cybercrime. Sometimes people are simply negligent about confidential information.
Why does cybercrime occur? - Financial Gain – This is the reason why the majority of cybercrimes occur. The attacker is looking for some sort of payout from committing the crime which could easily be immediate or indirect. In addition to simply stealing financial accounts, credit card, or other payment card information, some criminals will target private information for resale or blackmail.
- Information – Other cyberattacks are committed to target various forms of corporate information.
- Egoistical – This is likely to be the least common reason of the three, but some criminals will commit a crime simply to acknowledge the fact that they have the skills to defeat the security that companies or individuals have put in place.
Unfortunately, it may not be possible to completely eradicate cybercrime. However, there are many ways in which businesses can try and eradicate exposure to the crime by maintaining an effective cybersecurity strategy. - Create a cybersecurity incident response management plan that can help to support any policies and procedures you have already put in place.
- As soon as you gain new employees, you should train them on your cybersecurity policies and procedures, so they know how to protect data and what to do in the event of a security breach.
Employees could potentially be the biggest threat to your business. Although they may not be directly involved with the crime, they may be the reason that hacker gained access to your information. Chances are they will use poor passwords, giving hackers easy access. Hackers usually find passwords that include upper and lower case letters, numbers and other characters the hardest to hack.
- Make sure that all your websites and systems are up to date with all the current software releases and updates.
- Backup your data regularly in order to reduce the damage if there is a data breach.
- Protect your devices. You should aim to give your computers as much protection as possible. This can be achieved by installing an antivirus program like Bit Defender, ESET, Avast, or Malwarebytes and keeping it regularly updated, installing firewalls, and upgrading your operating system. Software developers take security very seriously, so the latest software versions will always come with the most up to date protection from cyberattacks.
- Hire a security expert. If, like many businesses, you are not experienced in preventing cyberattacks, your best option may be hiring professionals to do the job for you. Their job will be to routinely check all your systems for potential risks and mitigate the damages that expanding operations may cause.
If you could see the full list of potential cybercrimes out there, you may be tempted to stop using the internet entirely! These drastic actions will not be necessary if you simply protect yourself and take the necessary precautions that are outlined above. If you believe that you have been a victim of cybercrime, you should alert the police, even if this crime seems minor. You will be helping to prevent these criminals from committing crimes in the future. The post The Rise of Cybercrime and How to Prevent It appeared first on Burgess Forensics. ]]>https://burgessforensics.com/the-rise-of-cybercrime-and-how-to-prevent-it/feed/0 - Fitbit, Fun, Forensics, and Foeshttps://burgessforensics.com/fitbit-fun-forensics-and-foes/https://burgessforensics.com/fitbit-fun-forensics-and-foes/#respondWed, 08 Aug 2018 20:15:05 +0000https://burgessforensics.com/?p=11030Fitbit, Fun, Forensics, and Foes by Steve Burgess, 2018 Have you tracked your 10,000 steps today? Has anyone else tracked them? Fitness trackers are big business, […]
The post Fitbit, Fun, Forensics, and Foes appeared first on Burgess Forensics. ]]>Fitbit, Fun, Forensics, and Foesby Steve Burgess, 2018 Have you tracked your 10,000 steps today? Has anyone else tracked them? Fitness trackers are big business, helping people get and stay fit, and helping them share their progress with friends – and sometimes with strangers. Probably the most well-known of these devices (and apps) are the FitBit and apps paired with the Apple Watch, but also include the Moov Now, Samsung Gear Fit, Huawei Band, Tom Tom Spark, and about 350 others. The ability to map your movements is one of the more fun and attractive features about these devices. Stephen Lund is a cyclist and artist/GPS-doodler. He creates images by using a fitness tracker to map his movements on a bicycle. Here’s one of my favorites: 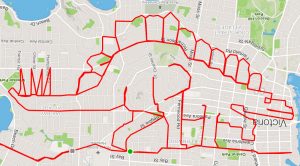 GPS doodle stegosaurus He gives a TEDx Talk about how this has helped him achieve fitness by combining rides with the fun of making these creations. FitBit data helps to catch a potential murderer. Fitness trackers in less light-hearted circumstances can provide evidence in the most serious of cases. At the end of 2015, Richard Dabate told Connecticut law enforcement a tale of a break-in where the robber killed his wife while he was fighting the intruder off. The problem was that subpoenaed records of her FitBit showed her active an hour after the murder was said to have taken place, and that she walked ten times further then what would have taken her into the now-fictional perp’s view. Along with other computer, FaceBook, and cellphone evidence, and the fact that Dabate had a pregnant girlfriend he was arrested for the crime. As of this writing, Mr. Dabate is still free on a million dollars bail. FitBit data helps an innocent man go free In May of 2016, Nicole Vander Heyder went out on the town in Green Bay, Wisconsin, but never came home. Her bloodied and naked body was found in a farm field nearby. Signs at first pointed to her boyfriend, Doug Detrie, who was arrested but nonetheless seemed shocked at the news and protested his innocence. Detrie was held on a million-dollar bond, but the apparent evidence (blood in the car, in the garage, and a suspicious spot on the sole of his shoe) didn’t hold up (blood in the car wasn’t the victim’s, blood in the garage wasn’t a human’s, and the suspicious spot wasn’t blood) so he was released. Data from Doug’s FitBit showed that he took only about a dozen steps during the time frame in which Nicole died. DNA evidence from Nicole’s clothes pointed at another man altogether, George Burch. Burch’s Android phone had Google Dashboard data associated with his Gmail account that showed GPS location data leading right to Nicole’s house. Eventually, he was charged, found guilty of first degree murder, and sentenced to life in prison where he still insists he’s innocent. FitBit data used to try to find a missing person In July of 2018, Iowa student, Mollie Tibbett went for a jog and hasn’t been seen since. Police have received her FitBit data in an attempt to locate her but haven’t released what they found in that data to the public. It appears that the geolocation information therein wasn’t enough to find her. Additional data from her cell phone and social media accounts has been sifted for clues, but as of August 6, 2018, there are no reports of her being found, although there appear to be people of interest. Hopefully location data from her FitBit will eventually help lead investigators to her current location. FitBit data banned by the military You may have heard news stories of late that the Army has expressed concern about military movements and security being compromised by data from fitness trackers and devices like the Apple Watch. A military official was quoted as saying, “The moment a soldier puts on a device that can record high-definition audio and video, take photos, and process and transmit data, it’s very possible for him or her to be tracked or to reveal military secrets … The use of wearables with Internet access, location information, and voice-calling functions should be considered a violation of national security regulations when used by military personnel.” But did you know that this news was from May 2015? And did you know it was a Chinese military official in the Chinese Army newspaper, the Liberation Army Daily? That’s right, some foreign governments have been banning such devices for years now. FitBit geolocation data banned by the US Military In 2013, the DOD distributed 2,500 FitBits to military personnel; in 2015 the Navy planned to run a pilot program to help the enlisted and their superiors keep track of fitness goals, and “allow Army leaders to track their Soldiers’ fitness in real time.” Aside from military members, Fitbit has a user base of over 10 million people. The information is viewable online, on a mobile device, or through the desktop application. Fitbit logs movement and allows users to log other health information in the app. Fitbit then uses this information to display progress over time. The manager of a companion app, called Strava, helps to map and display maps of subscribers’ movement using FitBit and other fitness tracking devices. In November 2017, Strava released their Global Heat Map of 3 trillion individual global GPS data points uploaded from the previous two years. Zooming in on the maps, as Australian security student Nathan Ruser did, revealed favored trails used in previously undisclosed bases by military fitness buffs. Below are trails around and in Mogadishu that could have provided potential targets of locations frequented by military personnel for Somalian dissidents.  Mogadishu fitness heatmap As one might imagine, the Army on August 7, 2018 banned use of geolocation features in iPhones, Apple Watch, FitBit and other fitness trackers with the following directive: “Effectively immediately, Defense Department personnel are prohibited from using geolocation features and functionality on government and non-government-issued devices, applications, and services while in locations designated as operational areas.” It hasn’t banned the use or possession of the devices altogether. The (FitBit) Law of Unintended Consequences There are three types of unintended consequences (according to Wikipedia)
An Unexpected benefit: A positive unexpected benefit – such as an accused murderer going free and shown to be innocent of charges due to his FitBit. Rather than showing the accomplishment of an athletic endeavor it instead showed inaction when the crime would have required much movement, as with Doug Detrie and Nicole Vander Heyder.
An Unexpected drawback: An unexpected detriment occurring in addition to the desired effect of the policy, such as a FitBit showing a purported victim of a crime instead being the perpetrator as with Richard Dabate and his wife.
A Perverse result: A perverse effect contrary to what was originally intended, as when military personnel using a FitBit to keep track of their fitness progress reveal themselves as potential targets to an adversary.
With any luck, none of these occasions will fall into lives of any of my readers. Keep fit, keep track, but be aware that you may be revealing more than you intend to. The post Fitbit, Fun, Forensics, and Foes appeared first on Burgess Forensics. ]]>https://burgessforensics.com/fitbit-fun-forensics-and-foes/feed/0 - The Case of the Deadbeat Beautyhttps://burgessforensics.com/case-deadbeat-beauty/https://burgessforensics.com/case-deadbeat-beauty/#respondMon, 07 Aug 2017 19:10:30 +0000http://burgessforensics.com/?p=10946Not everything always works out in Forensicland. Sometimes we strike out. In more ways than one. I was gazing out the tall windows of my office […]
The post The Case of the Deadbeat Beauty appeared first on Burgess Forensics. ]]>Not everything always works out in Forensicland. Sometimes we strike out. In more ways than one.I was gazing out the tall windows of my office at the blue, blue Santa Barbara sky, with nary a cloud in sight. It was my 50-something birthday. The bills were ignored. It seemed like a perfect day. Then the phone rang and a delightful voice answered. Ginger Justín. She laughed; she loved my jokes; she thought I was brilliant. She said I was perfect for her. As an expert. I reminded her of her dad. Her deceased dad. I should have taken the cue. It seems that Ms. Justín’s dad had passed away – possibly with the help of Lynn Dallas, live-in companion – a companion who was in the latest version of dad’s will. Not only that, Ginger – kind, caring, lovely Ginger – had been written out of the will. Her siblings were still in there. The grandkids were still in there. Ms. Dallas’s companion animal was in there, for dog’s sake! Money for the companion’s companion! But nothing for Ginger. Something had to be done. The poseur had to be exposed before she took yet another old man’s fortune. As Ginger informed me, this was Dallas’s M.O. Get to know the old guy, move in with him, become a love interest (“She never loved him; she was just after his money!”), then help him shuffle off the planet when the time was right. Ginger’s legal eagle, Big Dan Tuberosa, concurred. “This is a bad woman, this Dallas. She must be stopped.” So I asked for a catalog of devices that might hold various versions of the will. Mr. Justín had quite a setup. Racks with networking gear upstairs and down. Several computers and laptops. Lots of backup hard drives. Ginger asked if I could pick them up at estate administrator, John Geering’s place in Silicon Valley. And if I could cut this poor heroine break on the price. Thirty years of being in the biz has taught me the hard way that when someone tries to wheel & deal with you, it’s a red flag. Every dollar discount seems to come with a five-spot decrease in respect. It’s an odd part of human nature that giving away a C-note makes people think you’re an easy mark. But her desperate charm kicked in and I said I’d pick the gear up next time I was up that way. It turned out that Yahoo! News wanted my input for an online interview/article called: “True/False: Never Sell Your Old Phone,” so after the interview, I went to Geering’s nearby digs to fetch the stuff. When I came downstairs from his office, there was Ginger, waiting to greet me. She was long, lank, and lean, except where it counted. Her flaming red hair was alight with the afternoon sun. She leaned up against me with a languid, lasting hug and asked me to share a beer at a local sidewalk café, where we could discuss the case. I picked a table outside, in everyone’s view, just to play it safe. A local Firehouse IPA cooled my flushed face and settled my nerves enough to unaddle my wits. The roar in my ears subsided. I heard more about how much Ginger’s dad loved her. I heard more about how her siblings (the ones still mentioned in the Will) were relying on her to get the real story out, in their father’s memory. I heard how Ginger had to do this all by herself. I heard more about the evil Miss Dallas. I heard how this case would be worth tons of money and couldn’t I do part of my fee on a contingency basis? As it turns out, expert witnesses are not allowed to work on a contingency basis. The image of the hired gun would be inevitable. Regardless of the circumstances, being paid by how much you win just doesn’t fit with the ethics of complete honesty on the stand. Like the Lamas teach, attachment to the outcome just causes suffering. We still had the matter of a contract and a retainer to deal with. Big Dan assured me that Ginger was good for it, but it’s never a good idea to get started without something written down. She signed the contract and cut me a check. With this behind us and some tech talk put into lay terms, we decided on a strategy. She thought two computers (with 3 disk drives) would be most likely to bear fruit. • I would, of course, make a forensic image of each of the hard disks, using FTK Imager through a write blocker.
• Do a keyword search with EnCase for terms and phrases taken from known versions of the Will, and provide the results as a spreadsheet for each search term.
• Recover deleted files.
• Look for Willmaker documents, including by finding a hexadecimal signature for those files, then search and carve them out with Blade.
• Find when and on which computer there had been Wills created, modified and accessed.
• Provide a complete listing via spreadsheet of all files with Creation, Last Written, and Last Accessed Dates, amongst other file attributes.
• Dig up all existing and deleted History entries, using NetAnalysis and HstEx
• Find what USB devices had been attached to each computer (in case there were more discoverable devices).
• Find out if file-wiping software had been installed. As you might imagine, it took a bit of time and produced a whole lot of electronic documentation. This much data would take out a significant chunk of forest if I sent it as printouts. That many reams of paper aren’t free, and as I wasn’t working pro bono, the time to print it out wouldn’t be free. Facing the reality of having to pay for my time, Big Dan and Ginger agreed to take it as files even though they didn’t want any electronic correspondence to be able to be traced later. They wanted email communication to be mute on the subject of what we found. The CYA alarms inside started buzzing. More flags started going up…  Ginger spent many hours trying to sort through the data. I spent many hours on the phone explaining. She was bright, but her head just wasn’t built for electronic spreadsheets – it was built for storytelling, and she composed a storyline to fit her narrative. Ginger spent many hours trying to sort through the data. I spent many hours on the phone explaining. She was bright, but her head just wasn’t built for electronic spreadsheets – it was built for storytelling, and she composed a storyline to fit her narrative.
When I explained that the facts didn’t fit, she asked me in a throaty voice if I couldn’t please, please make this one adjustment to what I though the data meant? Through more red flags, I had to assume she was pulling my leg. The data is the data. As a famous TV cop once said, “Just the facts, Ma’am.” The defendant’s counsel agreed to take my deposition over the phone. When an attorney is getting ready to try to take me apart, I like to be able to read his body language, so phone depos are not my favorites. I could hear Big Dan and Ginger in the room, along with the other lawyer. We got into the subject of what modification, creation and access dates meant. As I explained, I could hear Ginger ask for a break to check on her son, who she said was sick at home. Then, my office phone rang and the number was hers! Her son was fine. She had called to try to change reality a bit. Though she had trouble finding her way around a spreadsheet, she insisted I was wrong in my testimony about file dates. I had to explain that I did know a thing or two about them, and that I had performed the experiments myself for confirmation. She had as well, she said, and I was wrong. I’ve got to admit, I was a little rattled. I tried to explain that Windows 7 and XP treat certain dates a little differently. I had to stick to my guns, and Ginger was furious. Still, they decided to take it all the way to court. Ginger prepared a stack of shreddable paper spreadsheets and faxed them to me. Now I was the one having trouble interpreting spreadsheets as I couldn’t make hers hold together. I did my best. No one wants a beautiful woman to think they are being scorned. Then she faxed me about a 100 points she wanted me to testify to. I spent more hours explaining that there were many things in there that I simply couldn’t say. I felt I was on a debate team. I should have quit then and there, but I stuck with it until she said -in writing – that if I couldn’t answer a particular point a particular way, she insisted that I say I didn’t know the answer. Even if that wouldn’t have been the height of an ethics breach, it would be perjury. I quit. 
I called Big Dan and told him I was taking myself off the case and that he really ought to tell his client not to ask an officer of the court to perjure himself. But Dan was still a believer in this terrible temptress. And court was looming. I let myself be talked into going to court under the following circumstances: Ginger wouldn’t talk to me any more – only lawyer Dan; nobody would try to influence my testimony, including Big Dan; and I had to receive immediate payment to cover the long-overdue bill as well as upcoming testimony. Done and done. I un-quit. Would that the agreement was kept. What should have been a few hours on the stand turned into two whole days. Ginger sat with her lawyer, scowling, shaking her head, and otherwise trying to get me to say the “right” things. Every one of her experts and her attorney and the judge was a doofus, and every one of the opposition’s was brilliant. The breaks were full of accusations and this pretty woman who could make so many people dance to her tune just couldn’t get the facts to say what she wanted them to, no matter how many times she changed her mind about what they ought to mean. They asked me to stay another day as a rebuttal witness to the next guy, but I just couldn’t. I had to deal with reality and appointments. Well, in the end, I was left holding the bag for a day’s court billing – and karma caught up with the toxic temptress. Maybe it was her histrionics, her fluid way with the truth, or just that Daddy had written her out of her inheritance for some odd reason. But after more years of working the court system, the evil Lynn Dallas ended up with what the Will deeded her and the shifty siren got a share of Karma. So now I sit, meditating on flags and signs and that blue Santa Barbara sky. Paying a little closer attention to what the universe has to show a guy that makes his living digging up the truth with a forensic spade. Trying to see what’s coming before the almighty has to hit me in the forehead with a sledge hammer to get my attention. And keeping the fancy duds pressed for that next court date with the facts. The post The Case of the Deadbeat Beauty appeared first on Burgess Forensics. ]]>https://burgessforensics.com/case-deadbeat-beauty/feed/0 - How to Avoid Being Hacked, Part 2 – Two-Factor Authenticationhttps://burgessforensics.com/avoid-hacked-part-2-two-factor-authentication/https://burgessforensics.com/avoid-hacked-part-2-two-factor-authentication/#commentsSun, 06 Aug 2017 00:37:06 +0000http://burgessforensics.com/?p=10940Multi-factor authentication (MFA) makes it much harder for a hacker to get access to your online stuff, and the most common form of consumer MFA is […]
The post How to Avoid Being Hacked, Part 2 – Two-Factor Authentication appeared first on Burgess Forensics. ]]>Multi-factor authentication (MFA) makes it much harder for a hacker to get access to your online stuff, and the most common form of consumer MFA is two-factor authentication (2FA). A very common form of 2FA is the debit card. One factor is the card itself, which contains magnetic identifying info (these days, a chip), and a PIN that you provide when you stick the thing in an ATM machine. It’s simple and fairly good at keeping others out of your ATM-accessible cash. 2FA is important for your online accounts, such as email and your iCloud accounts.While I admit it can be a bit of a pain to have to do something additional to get into your account, it’s far less of a pain than having one’s identity stolen, losing access to your email, or answering to your friends who wonder why you have said such crazy things about them (unless, of course, you actually said those crazy things!). Or, heaven forfend, someone logging in as you on one of your gaming accounts.  Here’s how 2FA or two-step authentication works for a couple of different online account types. (Note, these services change things up from time to time, so it’s good to keep abreast of such changes.) Here’s how 2FA or two-step authentication works for a couple of different online account types. (Note, these services change things up from time to time, so it’s good to keep abreast of such changes.)
Setting up Google 2-Step verification First you log in with user name and password (we’ll get to choosing smart passwords in Part 3) to your Gmail account. There should be an avatar in a circle near the upper-left hand corner of the window. Maybe it’s even a photo of you. Click on it and you’ll see “My Account.” (Incidentally, this changes every couple of years) On the new window that opens up, click on “Sign-in & security.” Click on “2-Step Verification,” then on “Get Started.” Time to enter your username and password again. Enter a phone number and click on whether you want to receive a text or a phone call. Then you magically get a text or phone call with a 6-digit verification code. Type it in and select the option to turn on 2-step verification. It’s that easy. Okay, it’s several steps, but not that hard. It may be that you prefer to collect your Gmail with some other app, like Outlook, rather than using a browser to go to the Gmail page for your mail. If so, it may be that once you’ve turned on two-step verification, your Outlook (or other app) keeps telling you that you have the wrong password, even though you know darn well it’s right. This has happened to me. You probably need to have Google give you a specific app password that Google will generate for you. You’ll need to go to the App passwords page, which at the time of this writing is at https://security.google.com/settings/security/apppasswords. Select the app you want it for (if Outlook, then you would select “Mail”), then the device you are using (Google magically presents a list of the devices you use with their services). Then select “Generate.” It will show you a 16-digit number in a yellow bar for you to use as your new password for that app (Outlook, eg) on that device (don’t enter the spaces). You can save that password in your app and you may need that number again in the future. Yahoo! Yahoo! is similar: sign into your account, go to the account security page, click on “two-step verification,” and toggle the button there to turn it on. Select an option to get a text or a phone call for verification. Enter the code that comes to you via text or phone call. At this point, you can create an app password, similar to the Google process above for your various apps like Outlook or Apple (iOS) Mail. iCloud Now, let’s set up 2FA on your iCloud account. First, you have to have a passcode set on your iPhone or iPad. Click on the Settings app. If your device uses iOS 10.3.3, click on your name (or the name of the account you use to sign on), then on “Passwords & Security.” Did I mention that this will change as Apple keeps us on our toes by changing everything up once we’ve gotten comfortable with the previous version? In the most recent previous version, you would have clicked on Settings, and then on iCloud, then your name, then Password & Security. But I digress… Now tap “Turn on two-factor authentication.” Be prepared to answer some security questions – which we’ll be discussing in a future article – and then enter the phone number where you want to receive the code for 2FA, and as previously, select whether you want a phone call or a text. Macintosh For a Mac, open System Preferences, and select iCloud, and then “Account Details.” You might have to login using your Apple credentials. As above, answer your security questions if it asks, enter the phone number where you want to receive calls or texts for verification. Once again, a magical robot instantly sends you the code and you have to enter that into the field that awaits your answer. Once it’s turned on, you’ll get a message asking for approval if an unknown device or location signs onto your account. Note that on a Mac, that notification can sometimes be on a window that is hidden behind another, so look for that if you find you’re having troubles with getting the approval request. Speaking of troubles, it seems like a lot of work to have two-factor authentication, but once it’s set up, it’s not too much of a pain and will add considerable safety to your accounts, as well as considerable barriers to potential hackers. So do it! Next time, we’ll discuss passwords, passcodes, and why you shouldn’t fill out those fun questionnaires that all of your friends send you. The post How to Avoid Being Hacked, Part 2 – Two-Factor Authentication appeared first on Burgess Forensics. ]]>https://burgessforensics.com/avoid-hacked-part-2-two-factor-authentication/feed/2 - How to Avoid Being Hacked, Part 1 – Emailhttps://burgessforensics.com/how-to-avoid-being-hacked-part-1-email/https://burgessforensics.com/how-to-avoid-being-hacked-part-1-email/#commentsTue, 01 Aug 2017 21:23:06 +0000http://burgessforensics.com/?p=10927How to Avoid Being Hacked, Part 1 – Email Hacking is a common occurrence these days, but it’s good to know that hacking targeting you specifically […]
The post How to Avoid Being Hacked, Part 1 – Email appeared first on Burgess Forensics. ]]>How to Avoid Being Hacked, Part 1 – EmailHacking is a common occurrence these days, but it’s good to know that hacking targeting you specifically because of who you are is far less common than scattershot hacking. Additionally, taking advantage of your online data is much more common than taking control of your computer. Most people don’t understand their computers or operating systems deeply. There’s no shame in that. No one really understands everything about computers. But that makes it easier for those types who are forever trying to make an illicit buck with some new way they have to separate you from your stuff, or some tool they’ve bought to apply leverage to an unprotected digital niche. Furthermore, the digital world changes quickly and it’s much easier for those providing software and hardware to sell insecure wares rather than to take the extra time (and loss of market share) to make them very safe. So it remains up to us to be more conscious in our behavior online, on the phone, and with our purchased equipment. Some of these conscious behaviors apply across the board to computers, tablets, and phones; others are specific to certain platforms. Email – Phishing I got an email from Apple, referencing a recent purchase and asking me to verify it. I clicked on the link and my browser went to Apple’s website, but something didn’t seem quite right. I stopped a moment to think: I had made a purchase online from Apple the previous day, but the email didn’t reference the specific item. I dropped off the website and took a look at the email. I hovered my cursor over the link and sure enough, it didn’t even mention Apple in the link. This is super-common – phishing emails designed to get you to go to some official-looking but bogus website (like the Apple website I’d thought I was on) and enter in your credentials which then give the hacker free access to your online account. And because many people use the same password and login for many of their online accounts it can give the hacker control of your digital life in short order. This happens to people who should know better and even almost happened to me, who also should know better! But how did they know I had just bought something from Apple, or in other bogus emails – how do they know I just bought something on eBay, or what bank I’m with? How do they even know my email address?  The short answer is – they probably don’t. They send that same email to a million likely email addresses – either from a list they bought, email addresses they harvested online, or just randomly generated by a program (joe@abc.com, joe@def.com, joe@yourwebsite.com, etc) . It costs almost nothing to send an email and it doesn’t cost much more to send a million. It’s easy enough to add an official logo snagged off a corporate website to an email, and it’s similarly easy to make an official-looking website. In fact, one could just snatch the code off an official website and replace the official links with bogus ones that steal your login credentials. Furthermore, a link isn’t always what it appears to be. For instance, if I say to click here to WinAMillionBucks.com you’ll see that it goes to a site that may save you some money, but won’t win you a million bucks. The short answer is – they probably don’t. They send that same email to a million likely email addresses – either from a list they bought, email addresses they harvested online, or just randomly generated by a program (joe@abc.com, joe@def.com, joe@yourwebsite.com, etc) . It costs almost nothing to send an email and it doesn’t cost much more to send a million. It’s easy enough to add an official logo snagged off a corporate website to an email, and it’s similarly easy to make an official-looking website. In fact, one could just snatch the code off an official website and replace the official links with bogus ones that steal your login credentials. Furthermore, a link isn’t always what it appears to be. For instance, if I say to click here to WinAMillionBucks.com you’ll see that it goes to a site that may save you some money, but won’t win you a million bucks.
It can be enlightening to hover (without clicking) your cursor over a given hyperlink like the one above, and see what pops up. Or if nothing pops up, right-click (on a single-button mouse, [ctrl]-click) to reveal the link. The short form answer to not being taken in like this is: DON’T click on links in emails. Type the desired URL into a browser. Or copy the link, paste it into a text document, and see if it is actually your bank, or Apple, or eBay or where you really wanted to go. Coming up in part 2: Two-Factor Authentication, Passwords, and Giving Away the Form. The post How to Avoid Being Hacked, Part 1 – Email appeared first on Burgess Forensics. ]]>https://burgessforensics.com/how-to-avoid-being-hacked-part-1-email/feed/2 - Keyword Searcheshttps://burgessforensics.com/keyword-searches/https://burgessforensics.com/keyword-searches/#respondThu, 20 Oct 2016 18:35:03 +0000http://burgessforensics.com/?p=10905Computer Forensics Expert Steve Burgess explains keyword searches – what they are, how to design an effective search, and differences between electronic data discovery (EDD) and […]
The post Keyword Searches appeared first on Burgess Forensics. ]]>Computer Forensics Expert Steve Burgess explains keyword searches – what they are, how to design an effective search, and differences between electronic data discovery (EDD) and computer forensics.The post Keyword Searches appeared first on Burgess Forensics. ]]>https://burgessforensics.com/keyword-searches/feed/0 - Data Recovery Myths and Misconceptionshttps://burgessforensics.com/data-recovery-myths-and-misconceptions/Mon, 22 Feb 2016 19:13:28 +0000http://burgessforensics.com/?p=10595In the very early 80’s, IBM introduced the IBM PC, progenitor of most modern personal computers. That same year, undoubtedly, the first PC hard disk failed […]
The post Data Recovery Myths and Misconceptions appeared first on Burgess Forensics. ]]>
Contact Steve Burgess: steve@burgessforensics.com
(866) 345-3345 ; (805) 349-7676
http://www.burgessforensics.com
|